Cryptography: Secure Communication & Data Protection
Comprehensive guide to cryptographic principles, encryption techniques, and information security. Explore the history, evolution, and practical applications of cryptography.
Introduction
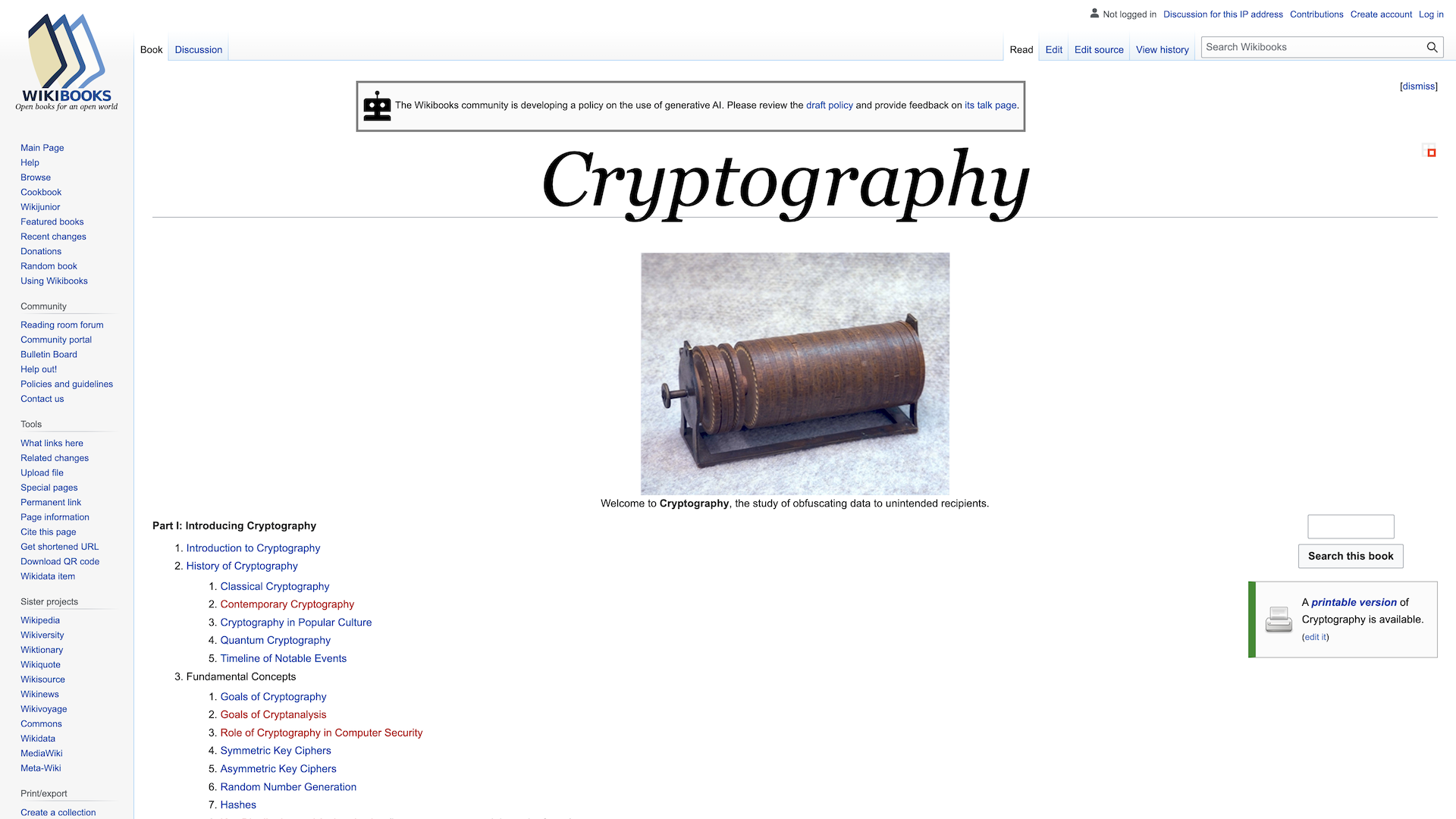
Cryptography is a comprehensive guide to the principles and practices of data security, encryption, and cryptographic techniques. It delves into the world of secure communication and the protection of data integrity, making it essential reading for anyone interested in information security.
Highlights
- Covers a wide range of cryptographic concepts, including symmetric and asymmetric key ciphers, hashes, random number generation, and key distribution
- Explores the history and evolution of cryptography, from classical methods to contemporary and quantum techniques
- Discusses common flaws and weaknesses in cryptographic systems, as well as secure password practices
- Provides a strong mathematical foundation for understanding cryptographic principles
Recommendation
This course is highly recommended for anyone interested in information security, data protection, or the technical aspects of cryptography. It offers a thorough and well-rounded introduction to the field, making it suitable for both beginners and those with prior knowledge in the subject.
How GetVM Works
Learn by Doing from Your Browser Sidebar

Access from Browser Sidebar
Simply install the browser extension and click to launch GetVM directly from your sidebar.

Select Your Playground
Choose your OS, IDE, or app from our playground library and launch it instantly.

Learn and Practice Side-by-Side
Practice within the VM while following tutorials or videos side-by-side. Save your work with Pro for easy continuity.
Explore Similar Hands-on Tutorials
Gray Hat Hacking: The Ethical Hackers Handbook
4Practical Cryptography for Developer
20Programming Differential Privacy
21The Joy of Cryptography (2021)
8Kali Linux 2018: Assuring Security by Penetration Testing, Fourth Edition
15Secure Programming HOWTO - Creating Secure Software
25Ethical Hacking | SQL Injection Attack Course
10Ethical Hacking From Scratch | Cybersecurity Course
20Linux for Hackers and Pentesters | Ethical Hacking, Penetration Testing
23Discover categories